Abstract
This document presents a formal framework for dynamically calibrating the core parameters of the Correlated Asset Price Oracle (CAPO) system, namely maxYearlyRatioGrowthPercent and snapshotRatio, through autonomous Risk Oracles. These parameters jointly enforce a time-weighted upper bound on the permissible growth of a yield-bearing asset’s exchange rate relative to its base asset, thereby protecting downstream protocols from artificial inflation and oracle manipulation.
Rather than relying on static limits or infrequent governance actions, the CAPO system leverages real-time analytics on yield behavior, reward distribution cadence, and market deviations to continuously constrain oracle outputs. The parameter maxYearlyRatioGrowthPercent defines the maximum annualized compound growth allowable in the asset’s exchange rate, while snapshotRatio, anchored by a past reference timestamp, serves as the historical baseline against which this growth is measured.
Importantly, the effectiveness of CAPO is contingent not only on defensively parameterizing maxYearlyRatioGrowthPercent, but also on updating snapshotRatio at regular intervals. Without timely snapshots, even well-bounded growth parameters can permit excessive drift between the oracle’s upper bound and the asset’s true economic behavior. Continuous snapshotRatio refreshes are therefore critical to ensuring that CAPO remains tight, responsive, and manipulation-resistant across a diverse range of yield-bearing asset types.
Risk Oracles act as autonomous agents that monitor these dynamics off-chain and reparameterize the CAPO system accordingly, enabling secure, low-overhead integration into protocols that depend on yield-sensitive exchange rates.
Overview of CAPO and the Importance of Risk Oracles
As detailed in the original CAPO framework, the system is architected to safeguard lending protocols against oracle-driven inflation vectors and donation-style exploits by imposing a deterministic, time-weighted upper bound on the exchange rate between a yield-bearing derivative (e.g., wstETH) and its base asset (e.g., stETH), capturing the upper envelope of organic yield accrual. This upper bound ensures that, even under adversarial conditions, such as unauthorized control of the price feed via compromised EOAs, centralized oracle dependencies, contract upgrade vulnerabilities, or donation attacks that exploit favorable exchange rate misalignments, the protocol remains protected against artificially inflated valuations that could otherwise be used to extract unbacked borrowing capacity or induce bad debt.
This enforcement is governed by three key parameters:
snapshotRatio: the reference exchange ratesnapshotTimestamp: time of referencemaxYearlyRatioGrowthPercent: the annualized cap on exchange rate growth
The maximum ratio is determined via:
function _getMaxRatio() internal view returns (int256) {
return
int256(_snapshotRatio + _maxRatioGrowthPerSecond * (block.timestamp - _snapshotTimestamp)
where maxRatioGrowthPerSecond = (snapshotRatio * maxYearlyRatioGrowthPercent)/SECONDS_PER_YEAR, effectively transforming a multiplicative derivation into fixed point arithmetic. To enforce temporal smoothing and prevent manipulation via micro-timeframe extrapolation, as discussed here, the snapshotRatio ensures the snapshot is taken at a sufficient temporal offset from the current block timestamp.
The snapshotRatio functions as the foundational reference rate from which the upper bound on the exchange rate, denoted maxRatio—is derived. The parameter maxRatioGrowthPerSecond thus imposes a cap on the permissible rate of change in maxRatio relative to the time elapsed between the snapshotTimestamp and the current timestamp. This structure inherently positions snapshotRatio as the anchor for time-weighted evolution, with maxRatioGrowthPerSecond encoding the maximal compound growth over time.
Importantly, this design implies that if snapshotRatio is not refreshed at a consistent cadence, the derived maxRatio becomes increasingly detached from real-world exchange rate dynamics. Over long intervals, the temporal averaging embedded in the model begins to dilute responsiveness, effectively introducing drift between the enforced upper bound and the actual prevailing rate.
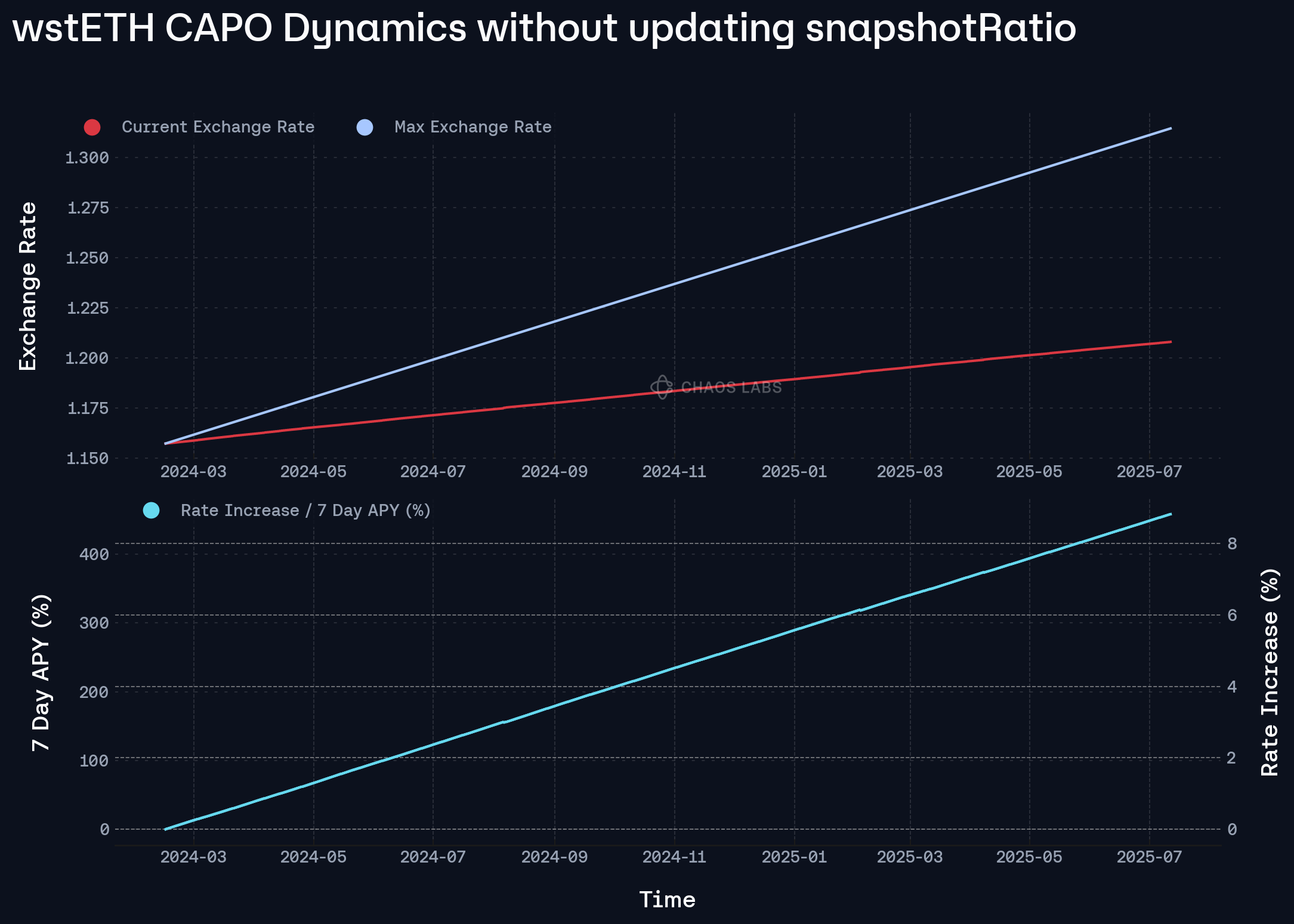
To illustrate this phenomenon, consider an example where maxRatioGrowthPerSecond is set to 9.68%, as wstETH is. If the factual growth in the exchange rate over the elapsed period is only 3.1%, then as the time delta increases, the upper bound maxRatio diverges significantly from the true rate. As observed below, the exchange rate can grow as much as 9% before reaching the upper bound during an inflation attack, which represents an equivalent 7 day APY of 450% in order to hit the upper bound. This growing discrepancy stems from the assumption of compounding at 9.68% per second, whereas reality reflects a much more tempered rate, thus highlighting the need for timely snapshotRatio updates to maintain effective control and fidelity in rate enforcement.
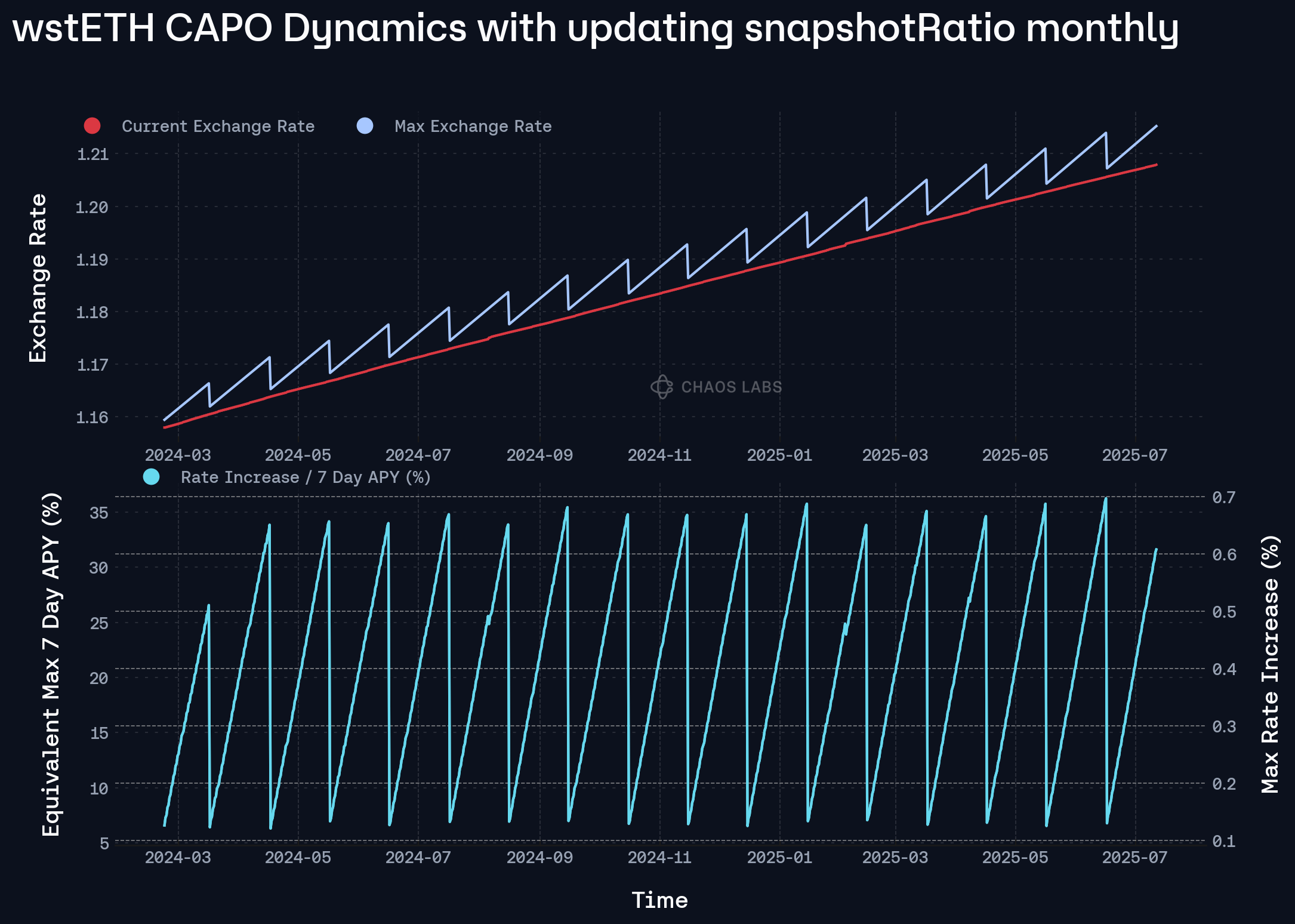
Assuming the snapshotRatio is updated monthly with a 7-day delay, the same maxYearlyRatioGrowthPercent constraint results in a substantially tighter upper bound on the exchange rate trajectory and its derived annualized growth. Empirically, the realized exchange rate remains within ~0.7% of the computed maximum exchange rate at all times, demonstrating effective rate bounding. Notably, this occurs even as the implied annualized growth, computed as a function of the local exchange rate delta, ranges between 12% and 37%. This discrepancy illustrates how regular snapshotRatio updates act as a mechanism for bounding short-term rate expansions, minimizing artificial inflation in annualized growth metrics induced by infrequent updates or stale snapshots.
Dynamic Responsiveness to Local Yield Spikes: Automating maxYearlyRatioGrowthPercent
In the general case, updating maxYearlyRatioGrowthPercent is a relatively frictionless and statistically grounded process. Most yield-bearing assets, such as those driven by lending interest, validator rewards, or liquidity mining, exhibit deterministic or semi-deterministic return profiles, enabling historical data to reliably inform an optimal cap value in a relatively infrequent manner. The CAPO algorithm leverages this regularity by using observed historical behavior to tune bounds that are both tight and appropriate, minimizing over-constraining during periods of normal growth. However, in assets with more sporadic or bursty yield distributions, where updates occur less frequently and snapshotTimestamp values may trail current conditions, large injections of rewards, such as DAO-driven emissions, retroactive drops, or sudden staking incentives, can cause abrupt local spikes. In these cases, the growth rate inferred from such snapshots can become outdated or unrepresentative, lagging behind the true yield trajectory.
Under the assumption that yield rates are experiencing local upward spikes, such that organic accrual temporarily approaches the configured maxYearlyRatioGrowthPercent, the CAPO algorithm, informed by its multidimensional parameter configuration, is designed to adaptively respond. It minimizes false positives by dynamically tightening or relaxing bounds in proportion to observed volatility, thereby reducing unnecessary artificial constraining during periods of legitimate growth. The parameter maxYearlyRatioGrowthPercent is computed as follows:
Update Decision Rule under Rate Escalation
Given the constraint that CAPO parameters can only be updated every 3 days, it is essential to design a conservative yet precise mechanism for deciding when to trigger an update of maxYearlyRatioGrowthPercent. The objective is to ensure that if a sudden escalation in staking yield begins, the CAPO mechanism still maintains an enforceable cap on the exchange rate before the next available update window. To achieve this, we introduce a decision rule that relies on short-term yield velocity as a proxy for immediate risk.
In contrast, under the assumption that observed rates decrease over time, per the algorithm above, the recommended output is derived as a function of the last 90 days of data, hence updating downward when necessary. In this context, the underlying “decision rule” is structured such that half of the defined maximum relative change serves as the threshold for permissible deviation, effectively acting as the trigger condition for downward rate updates.
Practical Examples and Backtesting
To illustrate the behavior and responsiveness of the rate calibration framework under varying market conditions, we present two contrasting case studies, ezETH and wstETH, analyzed through historical reward dynamics, APY trajectories, and parameter updates observed during recent backtesting.
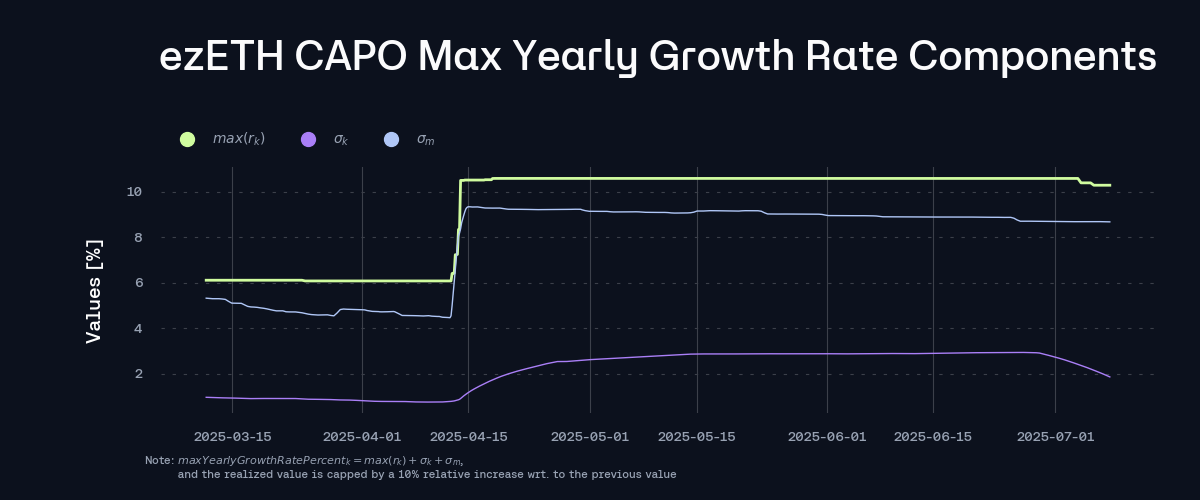
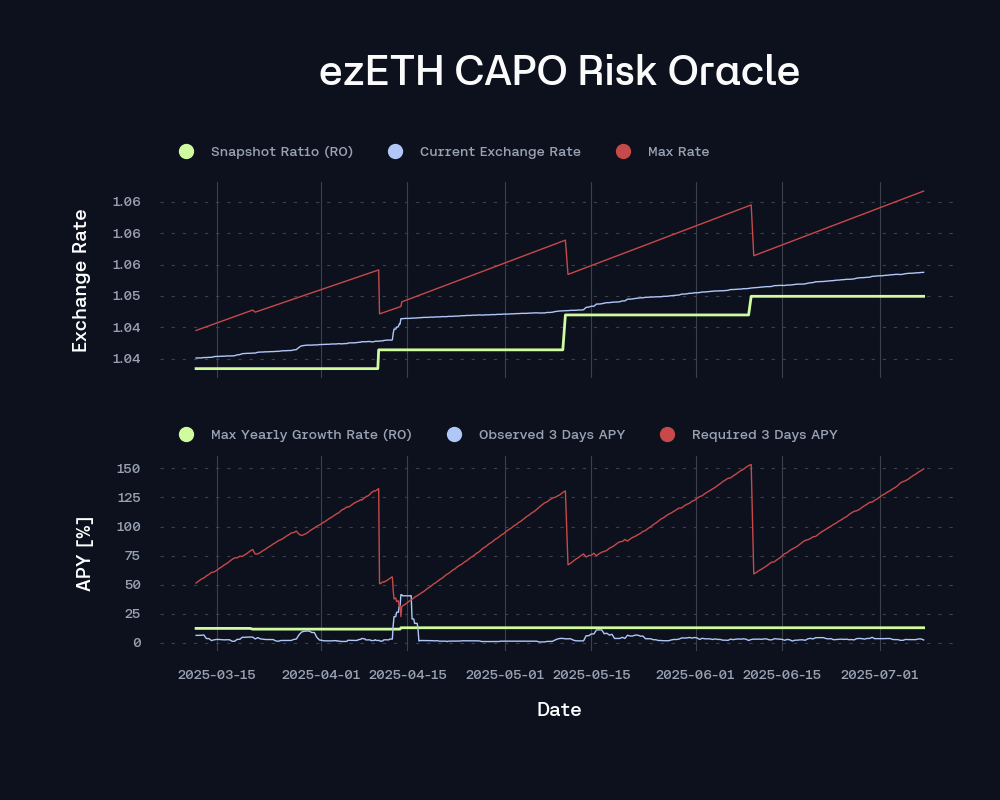
ezETH’s reward distribution has historically been highly irregular, characterized by intermittent and uneven emissions. In March, ezETH’s exchange rate experienced a notable upward distortion due to the protocol’s one-time injection and distribution of EIGEN rewards directly into the ezETH contract. This distribution materially inflated the exchange rate by increasing the cumulative rewards per token, effectively front-loading yield accrual. Prior to this event, the system exhibited significant short-term volatility in reward emissions and the associated annualized APY, as reflected in elevated dispersion metrics and an initially calibrated maximum rate of 12.38%.
Post-spike, the rate-setting algorithm executed a parameter recalibration in response to the updated reward trajectory. The underlying statistical properties, such as recent APY momentum and rate-of-change in cumulative rewards, registered an upward shift, thereby impacting the computed max rate recommendation. Crucially, the required minimum 3-day trailing APY, used as a guardrail to prevent excessive rate increases, converged below the observed realized 3-day APY. As a result, the updated max rate, governed by the 3-day constraint, was deemed optimal and within bounds, thereby increasing the associated maxYearlyGrowthPercent. The system thus exhibited resilience by adapting to the anomalous input while maintaining rate integrity and responsiveness.
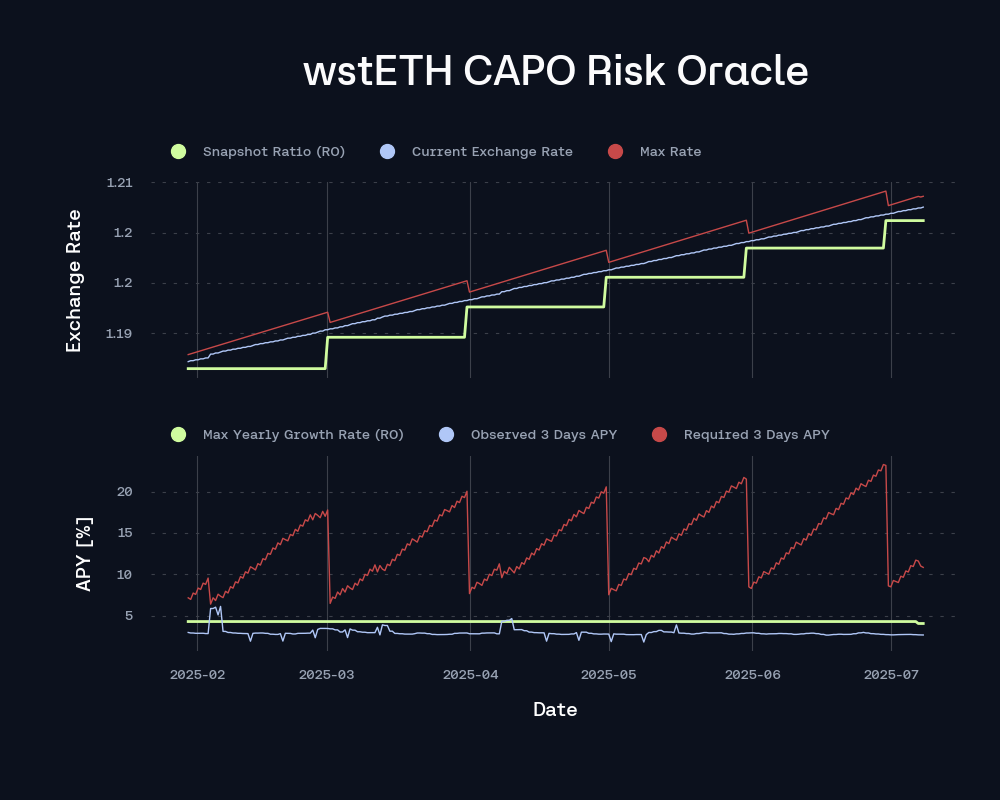
By contrast, wstETH exhibits highly deterministic rate growth and a stable state trajectory, which minimizes the need for active updates. The protocol operates under a dynamically constrained cap, continuously adjusted through real-time updates to the snapshotRatio. Given the low volatility and predictable accrual pattern, updates to the maxYearlyRatioGrowthPercent have been largely unnecessary, with the current value of 4.6% remaining sufficient to accommodate its steady yield progression.
Internally, while the effective recommended rate evolves, the magnitude of change remains within the tolerance defined by the existing maxYearlyRatioGrowthPercent, thereby not triggering an update. Specifically, the required 3-day APY has consistently remained below the observed 3-day APY, ensuring that the rate adjustment constraint remains satisfied. It is only toward the later stages of the observation window that we see a decline in the recommended rate, driven by the sustained smoothing of short-term yield signals, reflected in both the capped maximum rate and a concurrent reduction in measured volatility.
Proposed Parameter Constraints for CAPO Risk Oracle Updates
To maintain the integrity, predictability, and neutrality of the CAPO system, Risk Oracle parameter updates are subject to explicit constraints that govern their frequency and magnitude. These constraints are designed to ensure that CAPO remains a minimally trusted, credibly neutral mechanism, where bounded reactivity to market conditions does not come at the expense of system stability or over-centralized control.
snapshotRatio Constraint:
The snapshotRatio, which serves as the historical anchor for computing the time-weighted upper bound on exchange rates, can be updated at most once every 14 days and by no more than 5% relative to the prior value. The underlying algorithm will in practice only update once a month in most settings, representing an approximate upper bound of ~60% APR over a monthly horizon, aligned with aggressive but plausible yield scenarios.
Importantly, snapshotRatio is simply obtained from the relevant smart contract currently utilized to calculate the exchange rate for a given asset, at a given timestamp snapshotTimestamp, which adheres to the associated time-weighted logic expressed here (generally 7-14 days prior).
maxYearlyRatioGrowthPercent Constraint:
The parameter that controls the annualized rate ceiling can be adjusted once every 3 days, with a maximum 10% relative change per update. This strikes a balance between responsiveness to dynamic yield environments and measured, rate-limited evolution of the enforced cap.
| Parameter | Max Relative Change per Update | Timelock |
|---|---|---|
snapshotRatio |
5% | 14 Days |
maxYearlyRatioGrowthPercent |
10% | 3 Days |
Disclaimer
Chaos Labs has not been compensated by any third party for publishing this ARFC.
Copyright
Copyright and related rights waived via CC0